Ensure Proper Connectivity
Question
You are planning to set up an AWS VPN managed connection.
You have a customer gateway that is behind a NAT device.
In such a case, what steps should be taken to ensure proper connectivity? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and C.
Options B and D are incorrect since you need to mention the public IP address and ensure that UDP port 4500 is unblocked.
This is given in the AWS Documentation.
For more information on VPN Connections, please refer to the below URL.
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_VPN.html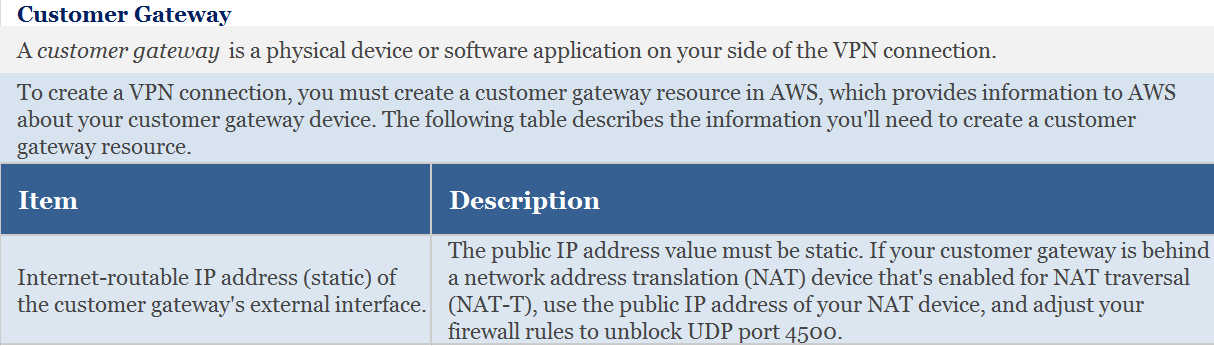
When setting up an AWS VPN managed connection and you have a customer gateway that is behind a NAT device, there are certain steps that need to be taken to ensure proper connectivity. Here are the steps:
Use the public IP address of the NAT device: You should use the public IP address of the NAT device instead of the private IP address of the customer gateway. The NAT device typically performs network address translation between the private IP address of the customer gateway and the public IP address that is visible to the internet. Therefore, the VPN connection should be established with the public IP address of the NAT device.
Ensure the on-premises firewall has UDP port 4500 unblocked: UDP port 4500 is used for NAT traversal, which is a technique that allows VPN traffic to pass through NAT devices. If the on-premises firewall blocks UDP port 4500, the VPN connection may not be able to establish or maintain a connection. Therefore, you should ensure that the on-premises firewall has UDP port 4500 unblocked.
In summary, the correct answers are A and C. You should use the public IP address of the NAT device and ensure that the on-premises firewall has UDP port 4500 unblocked to ensure proper connectivity when setting up an AWS VPN managed connection with a customer gateway that is behind a NAT device.
