Valid Concerns with a Public VIF
Question
Your company has set up an AWS Direct Connect connection along with a public VIF.
The IT security department raises a concern regarding the loopholes with a public VIF.
Which of the following is a valid concern that could be raised by the security department?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A.
This is provided in one of the Re-invent talks where the public IPs get advertised and are reachable via the public VIF.All other options are wrong since it's only the public IPs that get advertised.
For more information on the Reinvent video, one can visit the below URL.
https://www.youtube.com/watch?v=eNxPhHTN8gY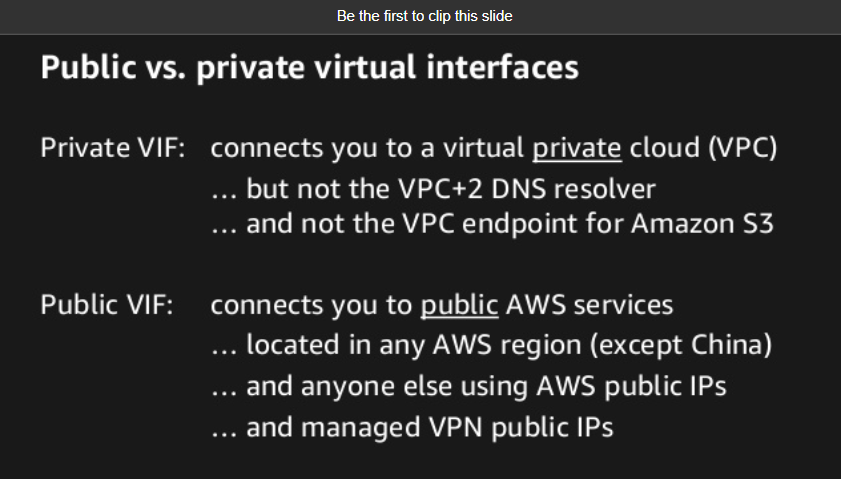
AWS Direct Connect is a network service that allows users to establish a dedicated network connection from their on-premises data center to AWS. The service provides a private, dedicated connection between the on-premises infrastructure and AWS, improving performance, reducing costs, and increasing security.
A public Virtual Interface (VIF) is a connection that allows traffic to flow between an AWS Direct Connect location and a public AWS service endpoint such as Amazon S3 or Amazon EC2. A public VIF is typically used when an organization needs to access public AWS services via a Direct Connect connection.
The concern raised by the IT security department regarding the public VIF is valid, as it can potentially expose the VPC to the Internet. The following is a detailed explanation of each option:
A. An EC2 instance with a public IP has a chance of reaching you via the public VIF. This is a valid concern because if an EC2 instance with a public IP address is configured to use the Direct Connect connection, it can potentially access the VPC through the public VIF. This could be a security issue, especially if the EC2 instance is not authorized to access the VPC.
B. An EC2 instance with a private IP has a chance of reaching you via the public VIF. This is not a valid concern as an EC2 instance with a private IP address cannot access the VPC through the public VIF. Private IP addresses are not routable over the public Internet, so it is not possible for an EC2 instance with a private IP address to access the VPC via a public VIF.
C. Your VPC gets exposed to the Internet. This is a valid concern as a public VIF provides a direct connection between the Direct Connect location and the public AWS services, potentially exposing the VPC to the Internet. This can be a security risk if the VPC is not properly secured and configured.
D. Your VPC gets exposed via the public VIF. This is a valid concern as a public VIF provides a potential path for traffic to flow between the Direct Connect location and the public Internet, potentially exposing the VPC to security risks. If the VPC is not properly secured and configured, it can be vulnerable to attacks and unauthorized access.
In summary, the valid concern raised by the IT security department is that a public VIF can potentially expose the VPC to the Internet, which can be a security risk if the VPC is not properly secured and configured.
