VPC Peering Connections
Question
You have created 3 VPCs, VPC A, VPC B and VPC C.
There is a VPC peering connection between VPC A and VPC B and a separate peering connection between VPC B and VPC C.
Which of the following is true with regards to this VPC peering arrangement?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
Since transitive peering is not allowed, you can use a proxy instance to forward the requests.
Options A, B and C are all invalid because, as per the AWS Documentation, this is the rule of transitive peering.
For more information on VPC peering configurations, please visit the below URL:
https://docs.aws.amazon.com/AmazonVPC/latest/PeeringGuide/invalid-peering-configurations.html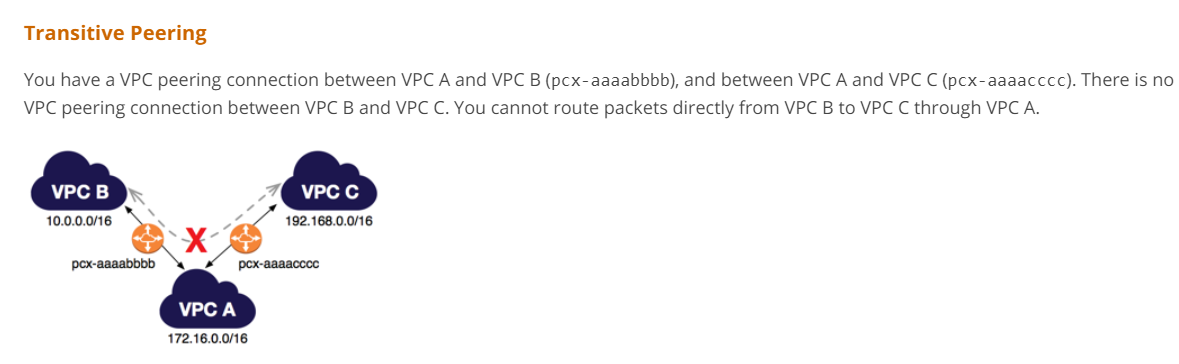
The correct answer is B: Instances launched in VPC A can reach instances in VPC C if the right routing entries are present.
VPC peering enables you to connect two VPCs together so that instances in either VPC can communicate with each other as if they are within the same network. In this scenario, there are two separate VPC peering connections between VPC A and VPC B, and between VPC B and VPC C.
When VPC A and VPC B are peered, the routing table of VPC A should be updated with a route for the VPC C CIDR block via the VPC B peering connection. This enables instances in VPC A to communicate with instances in VPC C through VPC B.
Similarly, when VPC B and VPC C are peered, the routing table of VPC C should be updated with a route for the VPC A CIDR block via the VPC B peering connection. This enables instances in VPC C to communicate with instances in VPC A through VPC B.
Therefore, instances launched in VPC A can reach instances in VPC C if the right routing entries are present. Security Groups do not play a role in this VPC peering arrangement as they are only used to control inbound and outbound traffic for instances within a VPC, not across different VPCs. There is no need to use a proxy instance to enable communication between VPC A and VPC C if the routing entries are properly configured.
