Achieving Complete End-to-End Encryption for HIPAA-Compliant Application Hosting
Question
Your company is planning to host an application on a set of EC2 Instances.
There is a requirement for complete end-to-end encryption for the data to ensure that the application is (HIPAA) compliant.
How can you achieve this?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
Since the data needs to be encrypted end to end, use an SSL certificate that can be mapped to the application.
AWS recommends TLS 1.2 or later.
Option A is incorrect because this can be used to encrypt data at rest.
Option B is incorrect because this will not encrypt traffic end to end.
Option C is incorrect because this is not a feasible option for this scenario.
Reference:
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/SSL-on-an-instance.htmlRefer to page 29 on the below link:
https://d0.awsstatic.com/whitepapers/compliance/AWS_HIPAA_Compliance_Whitepaper.pdf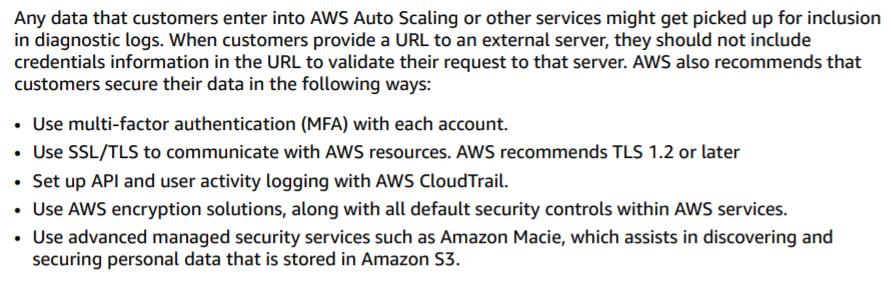
To achieve complete end-to-end encryption for the data in EC2 Instances and meet HIPAA compliance, the best option is to use TLS 1.2 or later to encrypt all the data. TLS stands for Transport Layer Security, which is a cryptographic protocol used to secure network communications. By using TLS, data is encrypted before transmission and decrypted after reception, ensuring that data remains confidential and secure throughout the entire process.
Option A, "Ensure that the traffic is encrypted using KMS" is not a valid option for end-to-end encryption. KMS, or Key Management Service, is a managed service that allows users to create and control the encryption keys used to encrypt their data. While KMS can be used to encrypt data at rest, it does not provide end-to-end encryption for data in transit.
Option B, "Set up a VPN connection between the EC2 Instance and the Internet" is another way to secure network communications. However, VPN only secures communication between the EC2 instance and the VPN gateway, not end-to-end. Also, VPN connections can be complicated to set up and may add additional latency to the network.
Option C, "Set up a Direct Connect connection between the EC2 Instance and the Internet" is not relevant to this scenario as Direct Connect is used to establish a dedicated network connection between an on-premises data center and AWS, bypassing the internet.
Therefore, the correct answer is option D, "Use TLS 1.2 or later to encrypt all the data". This option provides end-to-end encryption, ensuring that data is encrypted before transmission and decrypted after reception, and meets the HIPAA compliance requirement for complete end-to-end encryption.