Diagnosing Layer 4 Traffic
Question
You have VPC and EC2 Instances hosted in the subnet.
You need to diagnose layer 4 traffic and see which requests are ACCEPTED and REJECTED.
Which of the following would help in fulfilling this requirement?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - C.
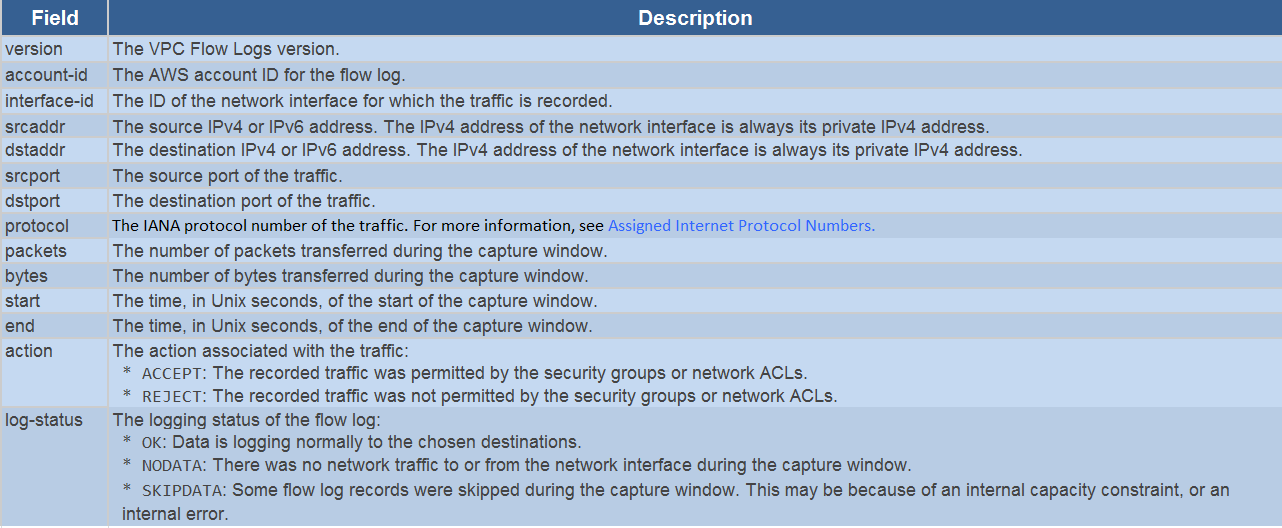
VPC Flow Logs can be used to fulfill this requirement.
Below is a snippet from the AWS Documentation which shows the fields which get recorded in VPC Flow logs.
For more information on VPC Flow logs, please refer to the below URL.
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/flow-logs.htmlNote:
The external devices can support only up to Layer 4 as given in the attached screenshot.
Also, note that VPC flow logs can be configured to support all the external devices' traffic to and fro from a VPC.
Therefore, VPC flow logs is compliant with all the corresponding protocols that are represented in each and every layer till Layer 4.
The correct answer for this question is C. Enabling VPC Flow Logs.
Here's why:
VPC Flow Logs allow you to capture information about the IP traffic going to and from network interfaces in a VPC. VPC Flow Logs can capture information about the source and destination IP addresses, the protocol used (TCP, UDP, ICMP, etc.), the source and destination ports, and the number of packets and bytes transmitted. You can also configure VPC Flow Logs to capture information about whether a packet was ACCEPTED or REJECTED by a network ACL or security group.
Option A, Enabling CloudTrail, is not the best answer for this question because CloudTrail is designed to capture API activity in AWS services, not network traffic.
Option B, Installing IDS on each Instance, would not be efficient as you would have to install IDS on every instance which could cause a lot of overheads. Also, IDS is designed to detect intrusions and attacks based on signatures or abnormal traffic behavior, not diagnose traffic.
Option D, Using Cloudwatch logs, is also not the best answer for this question because CloudWatch is designed to monitor and collect metrics, logs, and events from AWS resources and applications, not network traffic.
Therefore, the best option is to enable VPC Flow Logs to capture information about the IP traffic going to and from network interfaces in a VPC and diagnose layer 4 traffic and see which requests are ACCEPTED and REJECTED.