Troubleshooting Cloudfront ACM Certificate Visibility
Question
You have setup a Cloudfront distribution in AWS.
You want to use the AWS Certification Manager along with Cloudfront.
You are setting up Cloudfront, but you cannot see the ACM certificate that you created at an earlier stage to associate with the distribution.
What could be the underlying issue?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A.
The certificate needs to be configured in the North Virginia region.
This is also given in the AWS Documentation.
For more information on regions for ACM , please refer to the below URL.
https://docs.aws.amazon.com/acm/latest/userguide/acm-regions.html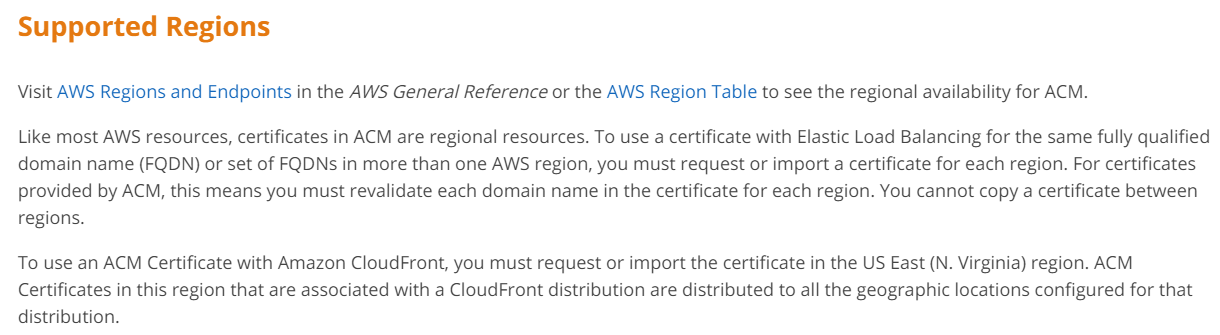
When setting up a Cloudfront distribution, you may want to use an SSL/TLS certificate issued by AWS Certificate Manager (ACM) to encrypt traffic between your viewers and Cloudfront.
If you cannot see the ACM certificate you created earlier to associate with the distribution, there could be several underlying issues:
A. You have not uploaded or created the certificate in the right region: It is important to create or upload the certificate in the same AWS region where the Cloudfront distribution is being created. If you create or upload the certificate in a different region, it will not be available to associate with the distribution.
B. You need to upload the certificate directly to Cloudfront after the distribution is created: After you create the certificate in ACM, you need to ensure that it is available in the region where you are creating the Cloudfront distribution. Then, you need to select the ACM certificate in the Cloudfront console or API when creating or updating the distribution.
C. You need to ensure that a CNAME record is created in Route 53 first: To associate an ACM certificate with a Cloudfront distribution, you need to validate that you own or control the domain name(s) listed in the certificate. One way to do this is by creating a CNAME record in Route 53 that maps the domain name to a Cloudfront distribution domain name. If the CNAME record is not created, ACM cannot validate the domain ownership, and the certificate will not be available for use with Cloudfront.
D. You need to ensure that an alias record is created in Route 53 first: Similar to CNAME record, you can create an alias record in Route 53 to map your domain name to your CloudFront distribution. However, unlike CNAME records, you can create alias records for the root domain (e.g., example.com) and not just subdomains (e.g., www.example.com). You must create an alias record in Route 53 that points to your CloudFront distribution's domain name in order to use an ACM SSL/TLS certificate with your distribution.
In conclusion, the most likely underlying issue could be that the ACM certificate was not created or uploaded in the right region, or a CNAME record or alias record was not created in Route 53 to validate domain ownership.