Firewall Configuration for AWS VPN Connection
Question
You are working to create a VPN connection between AWS and your on-premises infrastructure.
You've created the Virtual private gateway and the customer gateway.
You need to ensure the firewall rules are set on your side.
Which of the following would you configure? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.Answer - C and F.
This is given in the AWS Documentation.
All other options become incorrect because of the configuration mentioned in the AWS Documentation.
For more information on the firewall rules, please refer to page 34 in the below URL under the section "Configuring a firewall between the internet and your customer gateway device."
https://docs.aws.amazon.com/vpn/latest/s2svpn/s2s-vpn-user-guide.pdf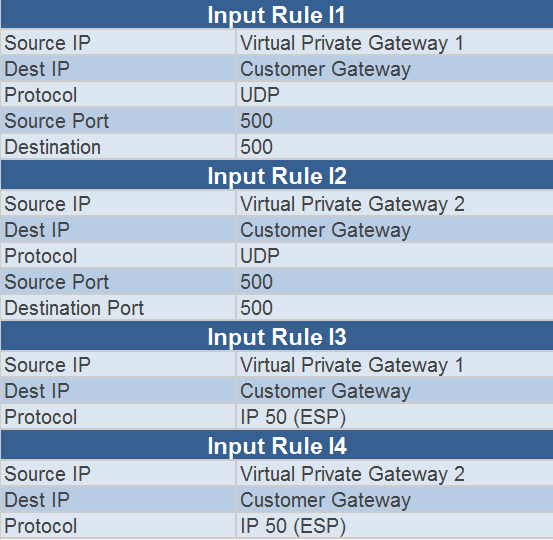
When creating a VPN connection between AWS and on-premises infrastructure, several components need to be configured, including Virtual private gateway, customer gateway, VPN connection, and routing.
Firewall rules should be set on the on-premises side to allow incoming traffic from the AWS side through the VPN connection. The following options are possible firewall rules that can be configured:
A. TCP port 500: This is the port used for Internet Key Exchange (IKE) negotiation. IKE is a protocol used to establish a secure and authenticated communication channel between two VPN endpoints. This port must be open for the VPN connection to be established.
B. TCP port 50: This port is not typically used in VPN connections.
C. UDP port 500: Similar to TCP port 500, this port is used for IKE negotiation and must be open for the VPN connection to be established.
D. UDP port 50: This port is not typically used in VPN connections.
E. IP protocol 5: This protocol is used for Internet Control Message Protocol (ICMP) redirects and is not typically used in VPN connections.
F. IP protocol 50: This protocol is used for the Encapsulating Security Payload (ESP) protocol, which is used to encrypt and authenticate data between VPN endpoints. This protocol must be allowed through the firewall for the VPN connection to function.
In summary, the firewall rules that should be configured on the on-premises side for a VPN connection with AWS are TCP port 500 and UDP port 500 for IKE negotiation, and IP protocol 50 for ESP traffic. Options B, D, and E are not typically used in VPN connections.