Tracking Invalid Login Attempts on AWS EC2 Instances
Question
I need to keep track of all invalid login attempts of a user when he tried to SSH to an EC2 instance.
How can I achieve that?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: A.
Option A is CORRECT.
Log data can be collected from EC2 instances by installing & configuring a CloudWatch Log Agent on the EC2 server.
These logs can then be delivered to CloudWatch log group streams, where they can be analyzed using Metric Filters.
Actions like notifying an admin on the invalid login attempt can then be done by defining CloudWatch alarms on the associated Log metrics.
Option B is incorrect.
CloudTrail tracks API requests made by users.
Its logs will be more useful when operations on resources are performed like creating an EC2 instance or terminating an EC2 instance.
Those logs can be integrated with CloudWatch for detecting abnormal operations on different AWS resources.
The user login scenario is captured as logs on the EC2 instance & sent to CloudWatch by the Log Agent.
When a user tries to SSH to an EC2 instance, the activity is not recorded in AWS CloudTrail as it is not an AWS API call.
Option C is incorrect.
Although it is possible to run a log utility to report failed login attempts by the user, it defeats the advantages that a centralized Monitoring & Logging system offers.
Also, by doing so, real-time monitoring will not happen due to the absence of streaming data resulting in delayed incident detection & resolution.
Option D is incorrect since the best way to track log data is to push it to a Log stream destination where it can be quickly monitored resulting in faster incident resolution.
Diagram:
References:
https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/WhatIsCloudWatchLogs.html https://aws.amazon.com/cloudwatch/ https://aws.amazon.com/cloudtrail/ https://www.tests.com/aws-monitoring-and-auditing/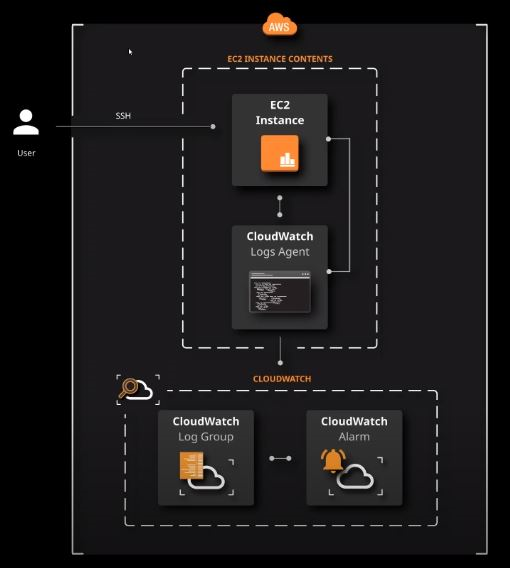
The correct answer is D. Both A and B options are correct.
To keep track of all invalid login attempts of a user when he tried to SSH to an EC2 instance, you can use AWS CloudWatch Logs and AWS CloudTrail.
AWS CloudWatch Logs allows you to monitor, store, and access log files from Amazon EC2 instances, AWS CloudTrail, and other AWS services. You can use CloudWatch Logs to collect and store log data from your EC2 instances, and then analyze and retrieve the data using CloudWatch Logs queries.
AWS CloudTrail is a service that provides a record of actions taken by a user, role, or an AWS service in your AWS account. You can use CloudTrail to log all user activity, including SSH login attempts to your EC2 instances.
To set up monitoring for invalid SSH login attempts, you can follow the below steps:
Create a CloudWatch Logs log group: This log group will store all the log data collected from your EC2 instances.
Install the CloudWatch Logs agent on your EC2 instances: The CloudWatch Logs agent allows you to collect and send log data to your CloudWatch Logs log group.
Configure the CloudWatch Logs agent to monitor SSH logins: You can configure the CloudWatch Logs agent to monitor the /var/log/secure log file on your EC2 instance. This file contains information about all SSH login attempts, including successful and unsuccessful ones.
Integrate CloudTrail with CloudWatch Logs: CloudTrail captures all SSH login attempts to your EC2 instances, and you can configure it to deliver data events captured by the login activity to a CloudWatch Logs log stream. This will allow you to monitor and analyze all SSH login attempts in one place.
By setting up CloudWatch Logs and CloudTrail in this way, you can monitor and track all SSH login attempts to your EC2 instances, including failed attempts. You can also set up alarms to notify you if there are too many failed login attempts or if there are suspicious login attempts from unknown IP addresses.