LDAP Authentication for VPC-Connected Application
Question
There is a requirement for an application hosted on a VPC to access the On-premises LDAP server.
The VPC and the On-premises location are connected via an IPSec VPN.
Which of the below are the right options for the application to authenticate each user.
Choose 2 answers from the options below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B and C.
When you have the need for an on-premises environment to work with a cloud environment, you would normally have 2 artifacts for authentication purposes.
An identity store - This is the on-premises store such as Active Directory which stores all the information for the users and the groups.
An identity broker - This is used as an intermediate agent between the on-premise location and the cloud environment.
In Windows you have a system known as Active Directory Federation services to provide this facility.
Hence in the above case, you need to have an identity broker who can work with the identity store and the Security Token service in AWS.
An example diagram of how this works from the AWS documentation is given below.
For more information on federated access, please visit the below link:
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios_federated-users.html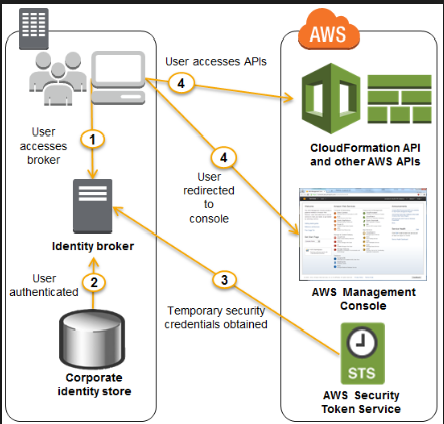
The scenario describes an application hosted on an Amazon Virtual Private Cloud (VPC) that needs to access an on-premises Lightweight Directory Access Protocol (LDAP) server via an IPsec VPN connection. The question asks which options are correct for authenticating users of the application.
Option A suggests developing an identity broker that authenticates against the IAM Security Token Service (STS) to obtain temporary AWS security credentials, which are then used by the application to access AWS services. This option is not applicable because it does not provide a mechanism to authenticate users of the application against LDAP.
Option B suggests that the application authenticates against LDAP and retrieves the name of an IAM role associated with the user. The application then uses the IAM Security Token Service to assume that IAM role and obtain temporary AWS security credentials. The application can use these temporary credentials to access any AWS resources. This option is a valid approach, and it can be implemented using AWS Security Token Service (STS) to grant users access to AWS resources.
Option C suggests developing an identity broker that authenticates against LDAP and then calls the IAM Security Token Service to obtain IAM federated user credentials. The application then uses these credentials to access the appropriate AWS services. This option is a valid approach, and it can be implemented using AWS STS to grant users access to AWS resources.
Option D suggests that the application authenticates against LDAP, and then uses the AWS Identity and Access Management (IAM) Security service to log in to IAM using the LDAP credentials. The application can then use the IAM temporary credentials to access the appropriate AWS service. This option is not applicable because there is no way to log in to IAM using LDAP credentials.
Therefore, the correct options are B and C, which both suggest using an identity broker to authenticate against LDAP and obtain temporary AWS security credentials using AWS STS. The application can then use these temporary credentials to access the appropriate AWS resources.