Configuring Custom Remediation Actions for AWS Config Rule on S3 Bucket Policies
Question
You are a DevOps engineer and you have an assignment to create a custom AWS Config rule to evaluate S3 buckets.
This rule checks whether S3 bucket resources have suitable bucket policies and if a certain bucket becomes non-compliant, remediation actions should be triggered immediately to fix the bucket policy.
You check the set of AWS recommended remediation actions but none of them are suitable for your case.
How would you configure your custom remediation actions in the AWS Config rule?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: C.
Option A is incorrect because you cannot select a Lambda function in the remediation action of an AWS Config rule.
The execution of remediation actions is achieved using AWS Systems Manager Automation.
Option B is incorrect because you should configure the remediation action in the AWS Config rule directly.
You do not need to create a CloudWatch Event rule or a Lambda function for this.
Option C is CORRECT because you can firstly create an automation document in AWS Systems Manager Automation and then select this document in the remediation action settings as follows:
Option D is incorrect because a CloudFormation template cannot be selected in the AWS Config rule's remediation actions.
You need to choose a custom automation document.
Reference:
https://docs.aws.amazon.com/config/latest/developerguide/remediation.html, https://docs.aws.amazon.com/systems-manager/latest/userguide/systems-manager-automation.html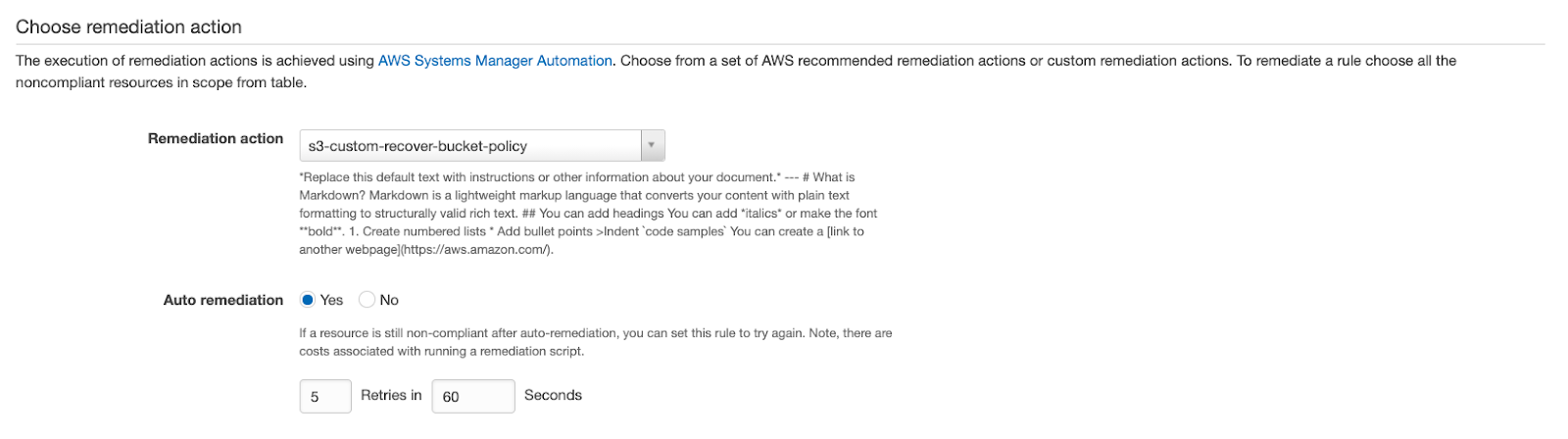
As a DevOps engineer, your task is to create a custom AWS Config rule that will evaluate S3 buckets for appropriate bucket policies. If a non-compliant bucket policy is detected, the rule should trigger remediation actions to fix the policy. However, the recommended remediation actions provided by AWS are not suitable for your case. In this scenario, you have to configure your custom remediation actions. Let's discuss each answer option to see which one is the best solution.
A. Create a Lambda function to recover the bucket policy and in the AWS Config rule, select the Lambda function to perform the remediation action.
This solution involves creating a Lambda function that recovers the bucket policy, and then selecting the Lambda function in the AWS Config rule to perform the remediation action. This solution is feasible as you can create a custom Lambda function to recover the policy in a way that meets your specific requirements. However, the solution may require significant development effort, and it may not be easy to maintain in the long run.
B. Create an AWS CloudWatch Event rule to check the state change of the Config rule. Trigger a Lambda function to automatically recover the S3 bucket policy.
This solution involves creating an AWS CloudWatch Event rule to monitor the state change of the Config rule. When a non-compliant bucket policy is detected, the CloudWatch Event rule triggers a Lambda function that automatically recovers the S3 bucket policy. This solution is also feasible, but it may require significant development effort, and it may not be easy to maintain in the long run.
C. Create a custom automation document in AWS Systems Manager Automation to fix the bucket policy. Select the automation document in the remediation action of the Config rule.
This solution involves creating a custom automation document in AWS Systems Manager Automation to fix the bucket policy. You can then select the automation document in the remediation action of the Config rule. This solution is a good option because AWS Systems Manager Automation is a service that allows you to create, manage, and execute automation workflows. You can create an automation document that meets your specific requirements to recover the bucket policy. This solution may require some effort to set up initially, but it should be relatively easy to maintain in the long run.
D. Create a CloudFormation template to restore the S3 bucket policy and select the template in the AWS Config rule's remediation action.
This solution involves creating a CloudFormation template to restore the S3 bucket policy. You can then select the template in the AWS Config rule's remediation action. This solution is also feasible, but it may require significant development effort, and it may not be easy to maintain in the long run.
In summary, the best solution is to create a custom automation document in AWS Systems Manager Automation to fix the bucket policy and select the automation document in the remediation action of the Config rule (Option C). This solution is a good option because AWS Systems Manager Automation is a service that allows you to create, manage, and execute automation workflows. You can create an automation document that meets your specific requirements to recover the bucket policy. This solution may require some effort to set up initially, but it should be relatively easy to maintain in the long run.