Accessing Credentials for Amazon RDS MySQL DB on AWS EC2 Instances
Question
You are using a configuration management system to manage your Amazon EC2 instances.
On your Amazon EC2 Instances, you want to store credentials for connecting to an Amazon RDS MYSQL DB instance.
How would you securely access these credentials when the number of connections per second is lesser than 500?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
When using IAM database authentication with Aurora MySQL, you are limited to a maximum of 500 new connections per second.
Refer to section "MySQL Limitations for IAM Database Authentication" on page 207 on the below link.
https://docs.aws.amazon.com/AmazonRDS/latest/AuroraUserGuide/aurora-ug.pdf#UsingWithRDS.IAMDBAuthFor more information, please refer to the below document link from AWS.
https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.IAMDBAuth.html https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.IAMDBAuth.IAMPolicy.htmlYou can use roles to delegate access to users, applications, or services that don't normally have access to your AWS resources.
For example, you might want to grant users in your AWS account access to resources they don't usually have, or grant users in one AWS account access to resources in another account.
Or you might want to allow a mobile app to use AWS resources, but not want to embed AWS keys within the app (where they can be difficult to rotate and where users can potentially extract them)
Sometimes you want to give AWS access to users who already have identities defined outside of AWS, such as in your corporate directory.
Or, you might want to grant access to your account to third parties so that they can perform an audit on your resources.
For more information on IAM Roles, please refer to the below document link: from AWS.
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles.html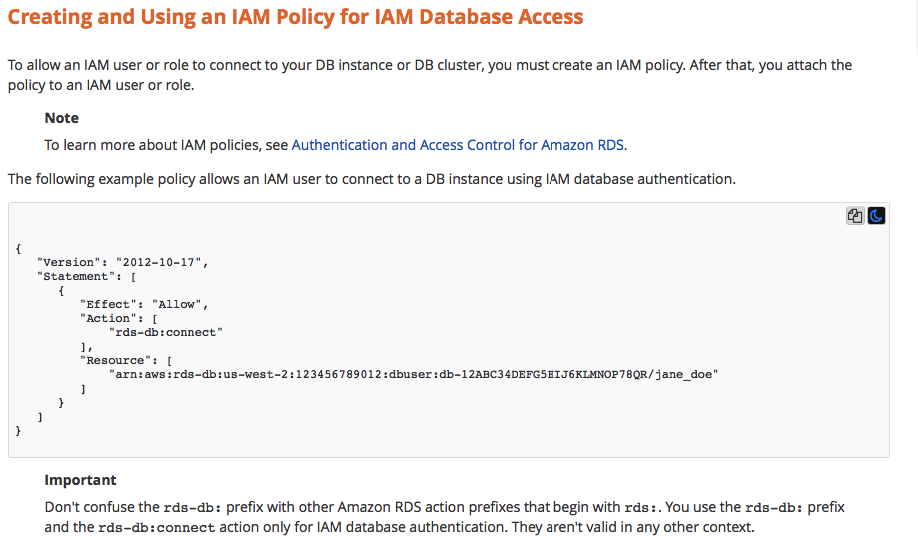
To securely access the credentials for connecting to an Amazon RDS MYSQL DB instance from your Amazon EC2 instances when the number of connections per second is lesser than 500, there are multiple options available.
A. Give the Amazon EC2 instances an IAM role that allows read access to a private Amazon S3 bucket. Store a file with database credentials in the Amazon S3 bucket. Have your configuration management system pull the file from the bucket when it is needed.
This option involves giving the Amazon EC2 instances an IAM role that allows read access to a private Amazon S3 bucket. The credentials for connecting to the Amazon RDS MYSQL DB instance are then stored in a file within the Amazon S3 bucket. The configuration management system can then be used to pull the file from the S3 bucket when it is needed. This option provides a secure way to store and access the credentials as the S3 bucket can be encrypted using server-side encryption, and the IAM role assigned to the EC2 instances can be restricted to only allow read access to the S3 bucket.
B. Launch an Amazon EC2 instance and use the configuration management system to bootstrap the instance with the Amazon RDS DB credentials. Create an AMI from this instance.
This option involves launching an Amazon EC2 instance and using the configuration management system to bootstrap the instance with the Amazon RDS DB credentials. Once the instance is configured with the credentials, an Amazon Machine Image (AMI) can be created from the instance. The AMI can then be used to launch new instances with the credentials preconfigured. This option provides a secure way to store and access the credentials as they are stored on the Amazon EC2 instances, which can be encrypted using EBS encryption, and the instances can be launched in a private subnet with restricted access.
C. Store the Amazon RDS DB credentials in Amazon EC2 user data. Import the credentials into the Instance on boot.
This option involves storing the Amazon RDS DB credentials in the user data of the Amazon EC2 instance. The configuration management system can then be used to import the credentials into the instance on boot. This option provides a less secure way to store and access the credentials as they are stored in plain text in the user data of the instance, which can be accessed by anyone with access to the instance.
D. Assign an IAM role to your Amazon EC2 instance, and use this IAM role to access the Amazon RDS DB from your Amazon EC2 instances.
This option involves assigning an IAM role to the Amazon EC2 instance and using this IAM role to access the Amazon RDS DB from the instance. The IAM role can be restricted to only allow access to the necessary resources, such as the Amazon RDS DB instance. This option provides a secure way to access the Amazon RDS DB instance as the credentials are not stored on the Amazon EC2 instances, and the IAM role assigned to the instances can be restricted to only allow access to the necessary resources.
In summary, option A and option B provide secure ways to store and access the credentials for connecting to an Amazon RDS MYSQL DB instance from your Amazon EC2 instances. Option C provides a less secure way to store and access the credentials, while option D provides a secure way to access the Amazon RDS DB instance without storing the credentials on the Amazon EC2 instances. The best option depends on the specific use case and security requirements.