Ensure S3 Bucket Encryption for Confidential Documents
Question
You've been asked to develop an application on the AWS Cloud.
The application will be used to store confidential documents in an S3 bucket.
You need to ensure that the bucket is defined in such a way that it does not accept objects that are not encrypted.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A.
The AWS Documentation gives an example on the same.
Option B is incorrect since the condition needs to be put in the Bucket policy.
Option C is incorrect since this is only used for MFA Delete for accidental deletion of objects.
Option D is incorrect since CORS is only used for cross-domain access.
For more information on using KMS Encryption for S3, please refer to the below link-
https://docs.aws.amazon.com/AmazonS3/latest/dev/UsingKMSEncryption.html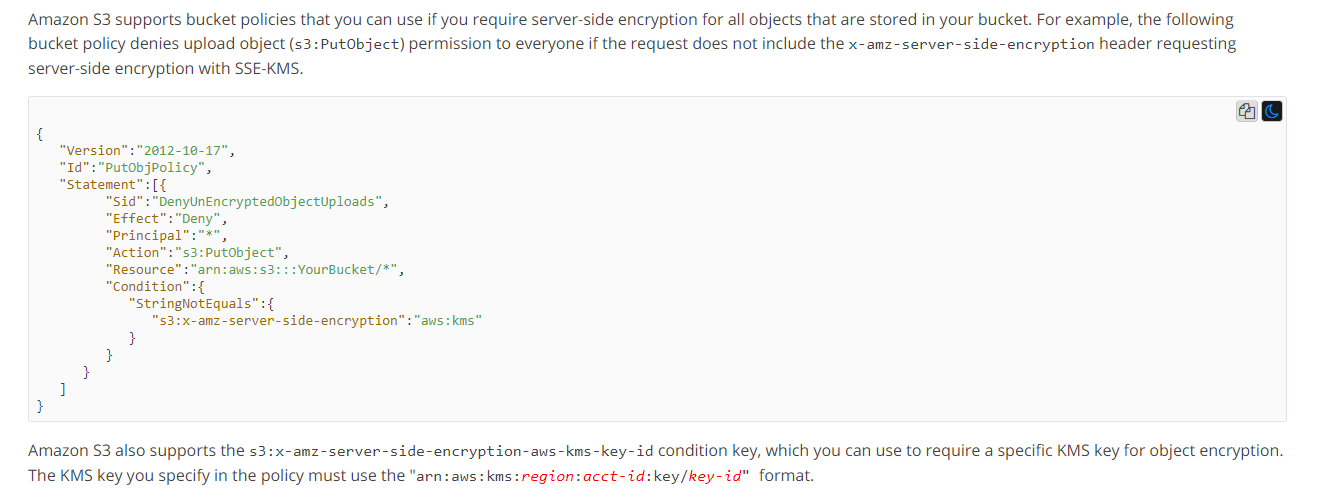
To ensure that the S3 bucket only accepts encrypted objects, you can enable default encryption for the bucket, and configure the bucket policy to require encrypted objects.
Here are the steps to achieve this:
Enable default encryption for the bucket:
- Go to the S3 console.
- Select the bucket that you want to enable encryption for.
- Click on the "Properties" tab.
- Click on the "Default encryption" section.
- Select "AES-256" or "AWS-KMS" as the default encryption type.
Configure the bucket policy to require encrypted objects:
Go to the S3 console.
Select the bucket that you want to configure the policy for.
Click on the "Permissions" tab.
Click on the "Bucket policy" section.
Add a statement to the policy that requires encryption for all objects uploaded to the bucket. Here is an example of what the policy might look like:
{ "Version":"2012-10-17", "Statement":[ { "Sid":"RequireEncryption", "Effect":"Deny", "Principal": "", "Action":"s3:PutObject", "Resource":"arn:aws:s3:::your-bucket-name/", "Condition":{ "StringNotEquals":{ "s3:x-amz-server-side-encryption":"AES256" } } } ] }
This policy statement denies any PutObject requests to the bucket that don't have the x-amz-server-side-encryption header set to AES256.
Option A is correct. You can ensure that the bucket only accepts encrypted objects by setting a condition in the bucket policy, as described above.
Option B is incorrect. IAM policies are used to grant or deny permissions to users or groups, and cannot be used to enforce encryption requirements on S3 objects.
Option C is incorrect. MFA (Multi-Factor Authentication) is a security feature that requires users to provide two or more forms of authentication to access AWS resources. It is not relevant to enforcing encryption requirements on S3 objects.
Option D is incorrect. CORS (Cross-Origin Resource Sharing) is a mechanism that allows web pages to make requests to a different domain than the one that served the web page. It is not relevant to enforcing encryption requirements on S3 objects.