Implementing Cross-Account IAM Roles for Secure Resource Access
Question
You are an AWS solutions architect in a large IT company, and your company has owned several AWS accounts.
By using IAM roles, access to resources in other accounts is granted.
For example, users in the Test account may switch roles and operate on DynamoDB resources that belong to the Dev account.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer - A, D.
The below diagram is a reference on how to switch roles between accounts.
Option A is CORRECT because you cannot switch to a role when you are signed in as the AWS account root user.
This is indicated in.
https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-account-with-roles.html.Option B is incorrect: Because multi-factor authentication (MFA) is optional when a role is created.
Option C is incorrect because the alias of the target account is optional.
During role switch, the user specifies the account ID (or alias) and role name.
Option D is CORRECT because it is required for the user to have permission to assume the role that belongs to other accounts.
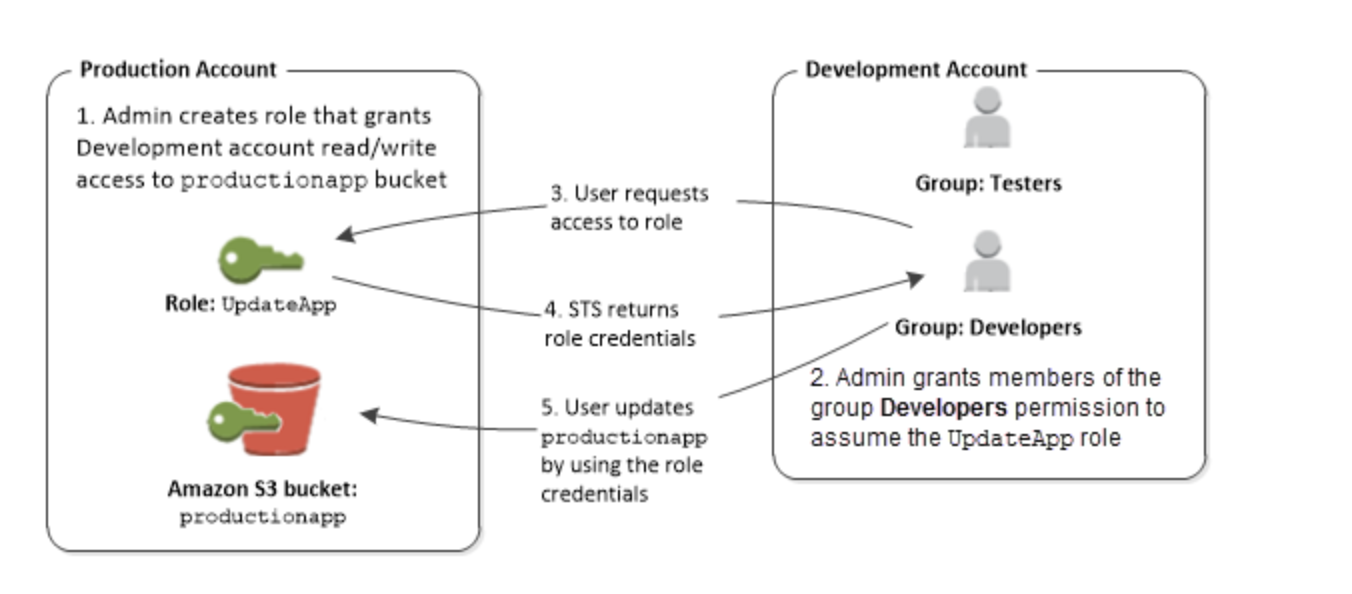
In a multi-account environment in AWS, IAM roles can be used to provide access to resources in other accounts. This allows users to switch roles and operate on resources that belong to a different account without having to sign out and sign in again as a user from that account.
To answer the question, we can break down each answer choice:
A. The user is signed in as the AWS account non-root user. This answer choice is not completely correct or relevant to the scenario given. It is good practice to avoid using the root account for regular tasks and to create non-root users with specific permissions, but it doesn't directly relate to IAM roles or accessing resources in other accounts.
B. The assuming entity has used multi-factor authentication (MFA) protection. MFA is a security feature that requires users to provide additional authentication factors besides their username and password when signing in to AWS accounts or assuming IAM roles. While MFA can add an extra layer of security, it is not a requirement for using IAM roles to access resources in other accounts.
C. The target account that the user plans to switch to must use an alias. This answer choice is incorrect. An account alias is a name for an AWS account that is easier to remember and use instead of an account ID number. However, it is not a requirement for using IAM roles to access resources in other accounts.
D. The user must be explicitly granted permission to assume the role. This answer choice is correct. In AWS, to assume an IAM role, a user must have permission to do so. The user can be granted permission by either adding the user to a group that has permission to assume the role or by attaching an inline policy to the user that allows them to assume the role. It is important to note that the user must have the correct permissions in both the source and target accounts to successfully switch roles and access the resources.
In conclusion, the correct answer to the question is D. The user must be explicitly granted permission to assume the role.