Connect Oracle RDS with S3 Bucket
Question
You are in charge of maintaining an Oracle database in RDS.
The development team tells you that the database instance needs to communicate with a new S3 bucket.
For example, it should be able to save the backup files to S3, and at the same time, it can fetch Oracle Data Pump files from the same bucket when required.
To connect the database instance with the particular S3 bucket successfully, which options are the prerequisites? (Select TWO.)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Correct Answer - A, E.
About how to transfer files between RDS Oracle and S3, please refer to the reference in https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/oracle-s3-integration.html.
Option A is CORRECT: Because the IAM role is required to allow the DB instance to interact with the S3 bucket.
Option B is incorrect: Because parameter group is not a necessary condition for this scenario.
Option C is incorrect: Because a new subnet group is not required.
The default subnet group also works.
Option D is incorrect: Because the S3 bucket does not need public access.
The RDS and S3 can communicate with each other under the same VPC.Option E is CORRECT: Because an option group that includes the S3_INTEGRATION option should be attached with the DB instance.
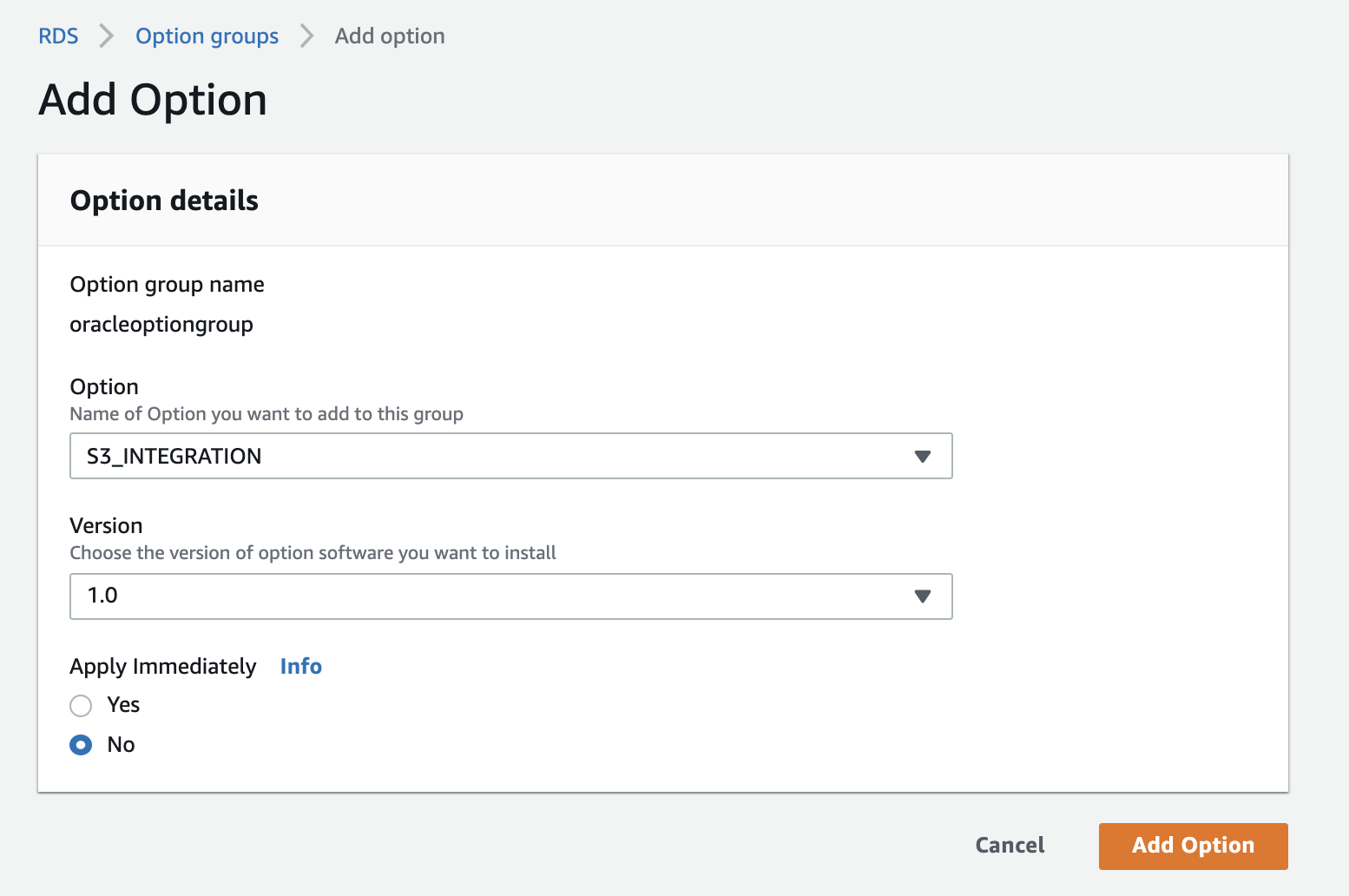
Check the below screenshot on how to add the S3_INTEGRATION option to the option group:
To connect an Oracle database instance in Amazon RDS to an S3 bucket, you need to configure several prerequisites. These are:
A. Configure an IAM role with a policy that allows to read and write the S3 bucket objects. Associate the role with the RDS instance.
You need to create an IAM role that allows the RDS instance to read and write objects in the S3 bucket. The policy should grant permissions to access the bucket, list objects in the bucket, and perform read and write operations on the objects. Once the role and policy are created, you need to associate the role with the RDS instance.
B. Create a parameter group that includes the parameter of the IAM S3 service role name. Attach the parameter group with the DB instance.
You also need to create a parameter group that includes the parameter of the IAM S3 service role name. This parameter specifies the IAM role that allows RDS to access the S3 bucket. After creating the parameter group, you need to attach it to the DB instance.
C. Configure a new DB subnet group. Link the DB instance with the subnet group.
If the RDS instance is not already linked to a DB subnet group, you need to create a new one and associate it with the RDS instance. The DB subnet group defines the subnets in which the RDS instance is located. The subnets must be in the same VPC as the S3 bucket.
D. For the new S3 bucket, ensure the Block Public Access settings are turned off. Enable the public access for the S3 bucket or add the S3 endpoint for the bucket.
You also need to ensure that the Block Public Access settings are turned off for the S3 bucket. This allows the RDS instance to access the bucket. If you don't want to enable public access, you can add the S3 endpoint for the bucket to the VPC route table.
E. Create an option group that includes the S3_INTEGRATION option. Associate the DB instance with the option group.
Finally, you need to create an option group that includes the S3_INTEGRATION option. This option enables the RDS instance to access the S3 bucket. After creating the option group, you need to associate it with the DB instance.
In summary, to connect an Oracle database instance in RDS to an S3 bucket, you need to create an IAM role with a policy that allows access to the bucket, create a parameter group that includes the IAM S3 service role name, link the DB instance with a DB subnet group, ensure that Block Public Access is turned off for the S3 bucket, and create an option group that includes the S3_INTEGRATION option and associate it with the DB instance.
