Detecting Employee IAM Permission Changes
Question
A security team is creating a response plan in the event an employee executes unauthorized actions on AWS infrastructure.
They want to include steps to determine if the employee's IAM permissions changed as part of the incident. What steps should the team document in the plan?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer is A.
Option A is CORRECT because you can use the AWS Config to view the history of a particular item.
AWS Config helps you review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines.
Option B is incorrect because AWS Macie is used for data security and data privacy to discover and protect your sensitive data in AWS.
It cannot be used to examine IAM permissions and monitor user activities.
Option C is incorrect because Cloud Trail is used to log and track API activity on your AWS environment.
They can monitor calls for IAM users but not give details on the permissions they have on AWS.
Option D is incorrect because AWS Trusted Advisor helps optimize your AWS infrastructure, increase security and performance, reduce your overall costs, and monitor service limits but it cannot give details on user activities and change of lAM permission on your AWS account.
Below snapshot provides an overview of user configuration and history using AWS Config.
For more information on AWS Config do refer the below URL:
https://aws.amazon.com/config https://aws.amazon.com/blogs/security/how-to-record-and-govern-your-iam-resource-configurations-using-aws-config/#:~:text=Setting%20up%20AWS%20Config%20is,not%20recorded%20by%20AWS%20Config.&text=A%20versioned%20history%20of%20AWS,configuration%20of%20those%20IAM%20entities.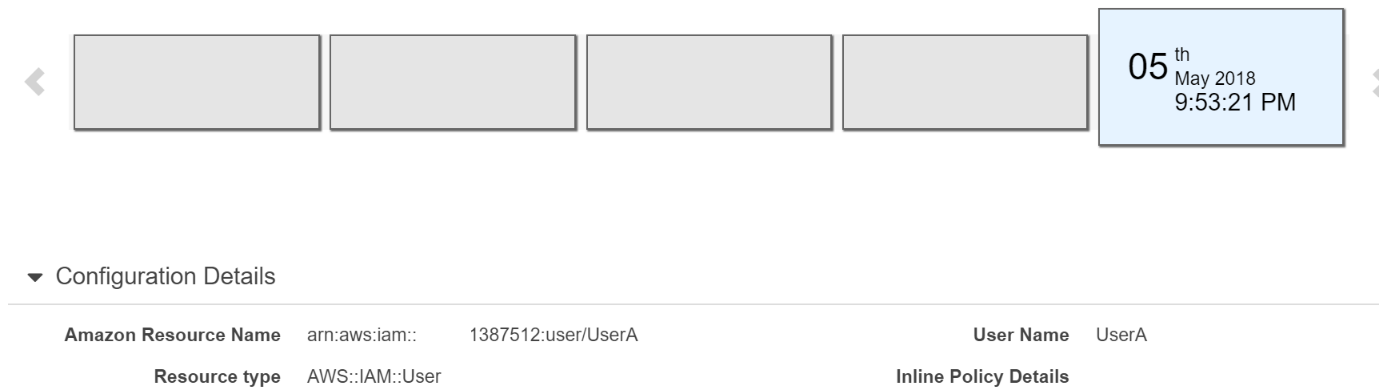
The security team is creating a response plan to detect unauthorized actions by employees on AWS infrastructure, and they want to determine if the employee's IAM permissions have been changed. IAM (Identity and Access Management) is a service that allows you to manage user access to AWS services and resources securely. IAM policies define permissions that determine what actions a user can perform on AWS resources.
To detect whether the employee's IAM permissions have changed, the security team should use CloudTrail. AWS CloudTrail is a service that records API calls made on your account, including IAM actions. By using CloudTrail, the security team can examine the employee's IAM permissions prior to the incident and compare them to the employee's current IAM permissions. This will help to determine if the employee's IAM permissions have changed, and if so, what changes were made.
AWS Config is a service that provides a detailed view of the configuration of AWS resources in your account. While it could be used to examine IAM permissions, it is not the best tool for this use case as it does not provide a detailed audit trail of changes made to IAM policies.
Macie is a service that uses machine learning to automatically discover, classify, and protect sensitive data in AWS. It is not suitable for this use case as it does not provide a mechanism to examine IAM permissions.
Trusted Advisor is a service that provides recommendations to help you optimize your AWS infrastructure for security, performance, and cost. While it could be used to examine IAM permissions, it does not provide a detailed audit trail of changes made to IAM policies.
In conclusion, the security team should document in their response plan to use CloudTrail to examine the employee's IAM permissions prior to the incident and compare them to the employee's current IAM permissions to determine if the employee's IAM permissions have been changed.