Control Access to RESTful API with AWS API Gateway and Lambda Function
Question
A team is developing a RESTful API for the annual leave data.
It should be used internally by employees.
An AWS API Gateway implements the API with the Lambda function. You want to control access to the RESTful API, and the incoming HTTP requests should include a valid token.
If the token is invalid, a 401 Unauthorized response will be returned. How would you configure the authorization for the API?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: B.
Option A is incorrect because a new Lambda function needs to be created as the authorizer.
The backend Lambda should not be involved.
Option B is CORRECT because a Lambda authorizer is useful if you want to implement a custom authorization scheme that uses a bearer token authentication strategy such as OAuth or SAML or uses request parameters to determine the caller's identity.
When a client makes a request to one of your API's methods, API Gateway calls your Lambda authorizer, which takes the caller's identity as input and returns an IAM policy as output.
Option C is incorrect because IAM policies in an API gateway cannot be used to evaluate a token header in the HTTP requests.
Option D is incorrect because although an AWS Cognito user pool can be configured as an authorizer of API gateway, it is not based on SAML.
The description in the option is incorrect.
Reference:
https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-use-lambda-authorizer.html.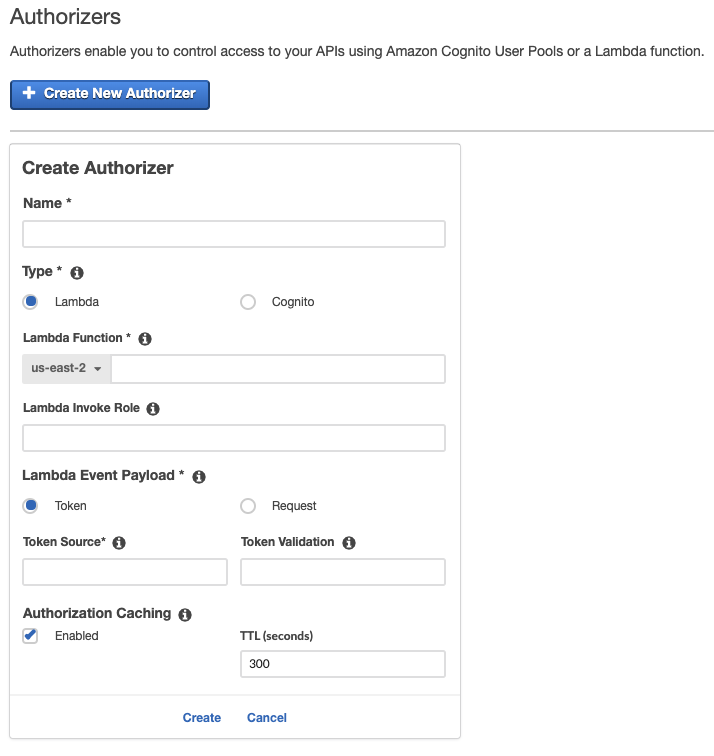
To control access to the RESTful API developed by the team, and to ensure that only authenticated users are able to access it, an authorization mechanism needs to be implemented. The mechanism should ensure that incoming HTTP requests include a valid token and return a 401 Unauthorized response if the token is invalid.
There are different ways to implement the authorization mechanism, but some common approaches are:
A. In the existing Lambda function, add an authorization logic to check the custom token header. Return a 401 Unauthorized response if the token header is invalid.
This approach involves modifying the existing Lambda function that implements the API to include an authorization logic that checks the custom token header. The Lambda function should validate the token and return a 401 Unauthorized response if the token header is invalid. This approach may work for simple use cases, but it has some limitations:
- It may require more development effort to modify the existing Lambda function.
- It may not be scalable or flexible enough to handle complex authorization requirements.
- It may not be easy to manage and maintain over time.
B. Create an authorizer for the API gateway using a new Lambda function. Implement the logic to validate the token in the new Lambda function.
This approach involves creating a new Lambda function that acts as an authorizer for the API Gateway. The authorizer Lambda function is responsible for validating the token and returning an IAM policy that defines the authorized actions for the user. The API Gateway then uses the IAM policy to allow or deny the API call. This approach offers several benefits:
- It allows for flexible and scalable authorization mechanisms.
- It can be used to implement complex authorization requirements.
- It can be managed and maintained easily over time.
C. Configure an IAM policy in the API gateway. Use the Principal field to determine which users are allowed to send requests to the API.
This approach involves configuring an IAM policy in the API Gateway to control access to the API. The policy defines which users or roles are allowed to access the API based on the Principal field. This approach may work for simple use cases, but it has some limitations:
- It may not be flexible or scalable enough to handle complex authorization requirements.
- It may not be easy to manage and maintain over time.
D. Configure a SAML authorizer using an AWS Cognito user pool and the token header is checked by Cognito. The API call proceeds only if the required token is valid.
This approach involves configuring a SAML authorizer in the API Gateway using an AWS Cognito user pool. The user pool is responsible for validating the token and returning an IAM policy that defines the authorized actions for the user. The API Gateway then uses the IAM policy to allow or deny the API call. This approach offers several benefits:
- It allows for flexible and scalable authorization mechanisms.
- It can be used to implement complex authorization requirements.
- It can be managed and maintained easily over time.
- It offers additional security features such as multi-factor authentication and user management.
In conclusion, the best approach to configure the authorization for the RESTful API will depend on the specific requirements and constraints of the use case. However, generally, option B or D may be the best choices, as they offer more flexibility and scalability than options A and C.