Required IAM Permissions for Kinesis Data Firehose and S3 Bucket Access
Question
You're planning to use Kinesis Data Firehose.
The data would be sent to an S3 bucket.
The data would be encrypted at rest using a KMS key.
You need to create an IAM role with suitable IAM policies to grant Kinesis Data Firehose access to the S3 bucket.
Which of the following permissions need to be included in the IAM policies? (Select TWO.)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and D.
If Kinesis Firehose needs to access an S3 bucket where encryption is enabled using KMS, the following permissions need to be included in the IAM policies.
Since the documentation clearly mentions what access needs to be given, the other options are invalid.
For more information on controlling access, please refer to the below URL.
https://docs.aws.amazon.com/firehose/latest/dev/controlling-access.html#using-iam-s3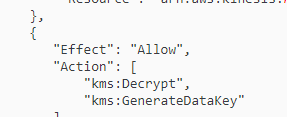
To grant Kinesis Data Firehose access to the S3 bucket, you need to create an IAM role with suitable IAM policies. Since you want to encrypt the data at rest using a KMS key, the IAM role should have permissions to use the KMS key for encrypting and decrypting the data.
The correct permissions that need to be included in the IAM policies are:
A. Kms:Decrypt: This permission allows the role to decrypt data using the KMS key. This is required as the data would be encrypted at rest using a KMS key and needs to be decrypted by the Kinesis Data Firehose before sending it to S3.
D. Kms:GenerateDataKey: This permission allows the role to generate a data key that can be used to encrypt the data. This is required as the Kinesis Data Firehose needs to encrypt the data using the KMS key before sending it to S3.
B, C are not required in this scenario. Kms:Import-key-material is not required because you are not importing any key material, you are using an existing KMS key. Kms:GenerateCustomerKey is not required because you are not generating a new KMS key, you are using an existing KMS key.
Therefore, the correct answers are A and D.