Determine Unauthorized IAM Permission Changes
Question
A security team is creating a response plan when an employee executes unauthorized actions on AWS infrastructure.
They want to include steps to determine if the employee's IAM permissions changed as part of the incident. What steps should the team document in the plan?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: A.
Option A is CORRECT because, with Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines.
Option B is incorrect because AWS Macie is used for data security and data privacy to discover and protect your sensitive data in AWS.
It cannot be used to examine IAM permissions and monitor user activities.
Option C is incorrect because Amazon GuardDuty is a threat detection service that continuously monitors malicious activity but does not give details on the IAM permissions.
Option D is incorrect because AWS Trusted Advisor helps optimize your AWS infrastructure, increase security and performance, reduce your overall costs, and monitor service limits, but it cannot give details on user activities or the change in lAM permissions.
The below snapshot shows an example configuration for a user in AWS Config:
For more information on tracking changes in AWS Config, please visit the below URL:
https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/TrackingChanges.html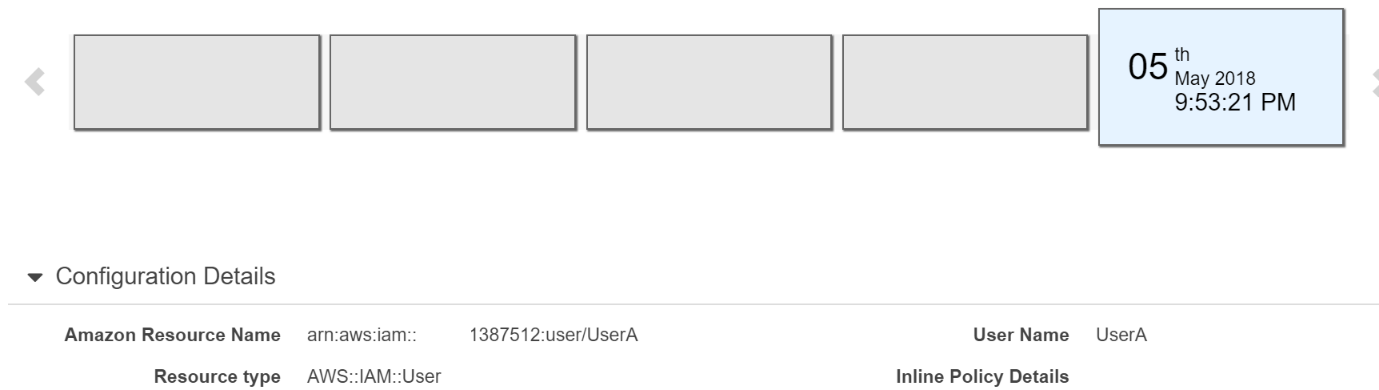
When an employee executes unauthorized actions on AWS infrastructure, it is important for the security team to quickly respond and investigate the incident to prevent further damage. One important step in the response plan is to determine if the employee's IAM permissions have changed as part of the incident. IAM (Identity and Access Management) is a service provided by AWS that enables the management of users, groups, and roles, and their associated permissions, that control access to AWS resources.
To achieve this, the security team can follow the steps below:
Identify the affected user: The security team should first identify the user who executed the unauthorized actions. This can be done by analyzing the logs from the affected AWS services.
Determine the IAM permissions before the incident: The security team should then determine the IAM permissions that the affected user had before the incident. This can be done by reviewing the user's IAM policies and permissions in AWS.
Determine the current IAM permissions: The security team should also determine the current IAM permissions of the affected user. This can be done by reviewing the user's IAM policies and permissions in AWS.
Compare the IAM permissions: The security team should compare the IAM permissions before the incident to the current IAM permissions of the affected user. This will help them identify if the user's IAM permissions were changed as part of the incident.
Given the above steps, the best option among the answer choices is Option A, which suggests using AWS Config to examine the employee's IAM permissions before the incident and compare them to the employee's current IAM permissions. AWS Config is a service that enables the recording of configurations and changes to AWS resources, including IAM policies and permissions. It can help the security team easily examine the user's IAM permissions before and after the incident and compare them to identify any changes made.
Option B, Macie, is a security service that uses machine learning to discover, classify, and protect sensitive data in AWS. It is not specifically designed for IAM permissions analysis.
Option C, Amazon GuardDuty, is a threat detection service that continuously monitors for malicious activity and unauthorized behavior in AWS accounts and workloads. While it can detect unauthorized access attempts, it is not specifically designed for IAM permissions analysis.
Option D, Trusted Advisor, is a service that provides guidance to help optimize AWS resources, improve security, and reduce costs. It is not specifically designed for IAM permissions analysis.