Operational Best Practices for Logging, S3, and EC2 in AWS
Question
You are working as a system administrator in a large financial company.
You need to assemble the compliance and security standards of the company, which includes various security, operational, and cost optimization checks in AWS.
The checks should include operational best practices for Logging, S3 and EC2
Which of the following is the most suitable to achieve the requirements?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: C.
Option A is incorrect because the requirement is to establish security, operational and cost optimization checks.
Security Hub focuses on security status, and the AWS Foundational Security Best Practices checks can not cover the security, operational and cost optimization checks.
Option B is incorrect because a single AWS Config rule and a Lambda function would be inappropriate to perform all the checks required for the company.
Lambda functions also have an execution time limit.
Ideally, it needs multiple AWS Config rules for this task.
Option C is CORRECT because AWS Config Conformance Packs are collections of AWS Config rules and remediation actions that can be easily deployed.
AWS provides lots of sample templates, and users can upload their own templates:
Option D is incorrect because Macie is a service to discover sensitive data across all of the organization's S3 buckets.
However, it does not help to perform other security or operational checks.
References:
https://docs.aws.amazon.com/config/latest/developerguide/conformance-pack-console.html, https://aws.amazon.com/security-hub/faqs/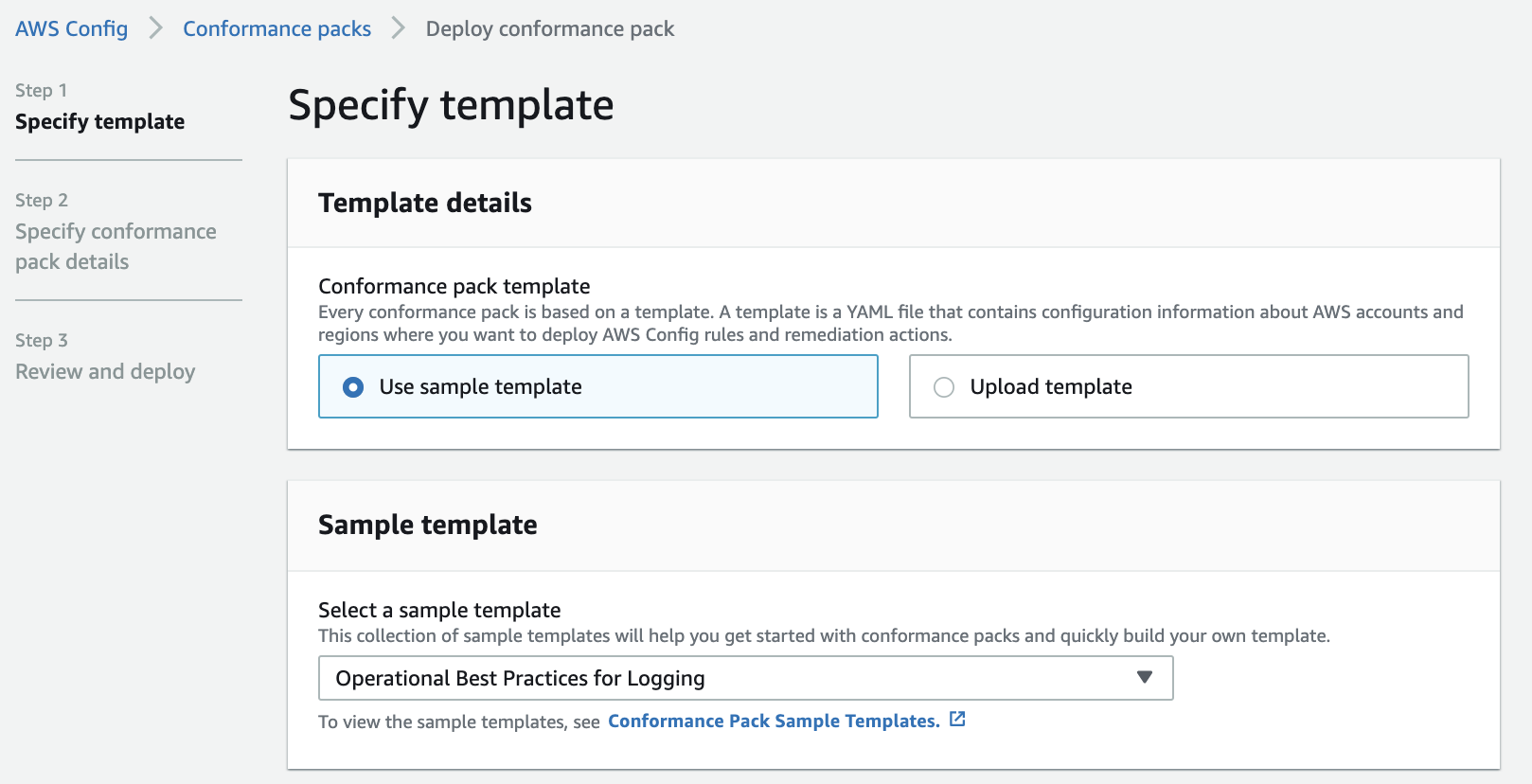
Option A: Enable AWS Security Hub and also enable the default AWS Foundational Security Best Practices checks for continuous monitoring. AWS Security Hub is a security service that provides a comprehensive view of security alerts and compliance status across AWS accounts. It offers a dashboard that aggregates and prioritizes security findings from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, and AWS Config. Additionally, Security Hub provides a set of pre-built compliance checks based on AWS Foundational Security Best Practices, which are continuously updated by AWS to keep up with the latest security threats and vulnerabilities. By enabling Security Hub and the AWS Foundational Security Best Practices checks, you can get visibility into your AWS environment's security posture, prioritize the most critical findings, and quickly remediate them.
Option B: Create a custom AWS Config rule with a Lambda function to perform the checks and remediation. AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources continuously. You can create custom AWS Config rules using AWS Lambda functions to evaluate the resources' configurations based on specific criteria. In this option, you can create custom Config rules that perform the checks and remediation actions required for compliance and security standards. You can use AWS Config's capabilities to monitor the resources' configuration changes and automate remediation actions using Lambda functions.
Option C: Create AWS Config rules and remediation actions with Conformance Packs based on YAML templates. AWS Config Conformance Packs are collections of AWS Config rules and remediation actions that enable you to evaluate the configurations of your AWS resources against specific compliance requirements. Conformance Packs are based on YAML templates, which define the AWS Config rules, their parameters, and the remediation actions. With Conformance Packs, you can easily apply compliance and security standards across multiple AWS accounts and regions. In this option, you can create Conformance Packs based on the company's compliance and security requirements, including the operational best practices for Logging, S3, and EC2.
Option D: Enable Amazon Macie to establish the required security and non-security company standards. Configure CloudWatch for monitoring and Lambda functions for remediation. Amazon Macie is a fully managed data security and privacy service that uses machine learning and pattern matching to discover and classify sensitive data in AWS. It can help you meet regulatory compliance requirements by identifying sensitive data, such as personally identifiable information (PII), intellectual property (IP), and financial data. Additionally, you can configure Amazon CloudWatch to monitor Macie's findings and set up Lambda functions to remediate any issues automatically. However, this option might not be the most suitable for achieving the operational best practices for Logging, S3, and EC2, which are not directly related to data security and privacy.
Considering the requirements mentioned in the question, option A is the most suitable for achieving the compliance and security standards for the company. By enabling AWS Security Hub and the default AWS Foundational Security Best Practices checks, you can continuously monitor and assess the security posture of your AWS environment, including operational best practices for Logging, S3, and EC2. Option B and C are also valid options, but they require more configuration and maintenance effort than option A. Option D might not be the best fit for achieving the specific requirements mentioned in the question.