Encrypting Traffic for AWS RDS Instances
Question
Your company is planning to host a set of databases using the AWS RDS service.
The IT security department has mandated that all traffic is encrypted in transit.
How can you achieve this with a database instance created with the AWS RDS service? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answers: A and B.
This is given in the AWS Documentation.
An example of the Microsoft SQL server is given below.
Option C is incorrect since you don't have access to the underlying server.
Option D is incorrect since the KMS service can't be used to encrypt the traffic.
For more information on this example, please refer to the below URL-
https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/SQLServer.Concepts.General.SSL.Using.html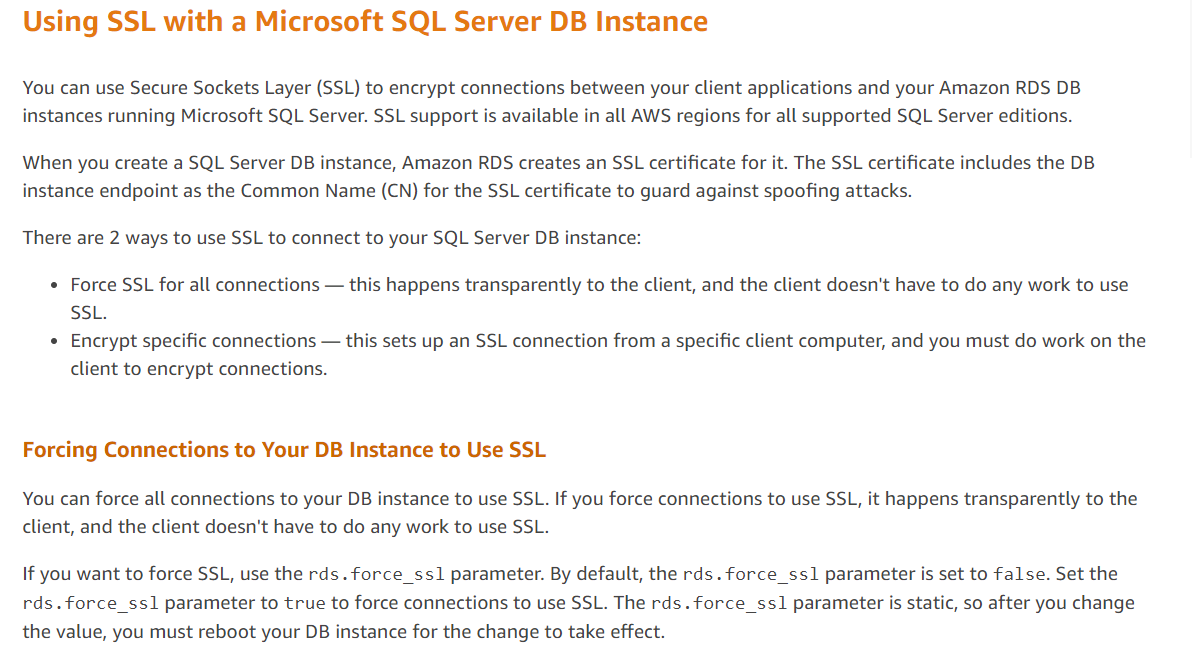
To achieve encryption of traffic in transit for a database instance created with the AWS RDS service, there are two possible solutions. These solutions are:
A. Use the SSL certificates provided by the AWS RDS service: One of the methods to enable encryption in transit for an RDS instance is to use SSL certificates provided by the AWS RDS service. This method works by creating an SSL certificate in the Amazon RDS and enabling SSL for the database instance. This can be done using the AWS Management Console, AWS CLI, or the Amazon RDS API. By enabling SSL, the client establishes a secure connection to the RDS instance using the SSL certificate.
B. Use the KMS service to encrypt the traffic: Another method to encrypt traffic in transit is to use the Key Management Service (KMS) in AWS. This method works by encrypting the data at the application level before it is transmitted to the RDS instance. This can be done by using the AWS SDK or an encryption library that supports AWS KMS. By encrypting data at the application level, the data remains encrypted until it reaches the RDS instance, even if the network connection is compromised.
C. and D. are incorrect answers: C. Using .pem keys files that come for the underlying server is not a method for encrypting traffic in transit for an RDS instance. This method is used to authenticate and establish a secure connection between a client and a Linux-based server.
D. Using the Parameter Group for the RDS Instance is not a method for encrypting traffic in transit for an RDS instance. The Parameter Group is used to configure the RDS instance's database engine and related settings. It does not provide a way to encrypt traffic in transit.
