Question 78 of 247 from exam AZ-104: Microsoft Azure Administrator
Question
HOTSPOT -
You have an Azure subscription named Subscription1.
In Subscription1, you create an Azure file share named share1.
You create a shared access signature (SAS) named SAS1 as shown in the following exhibit:
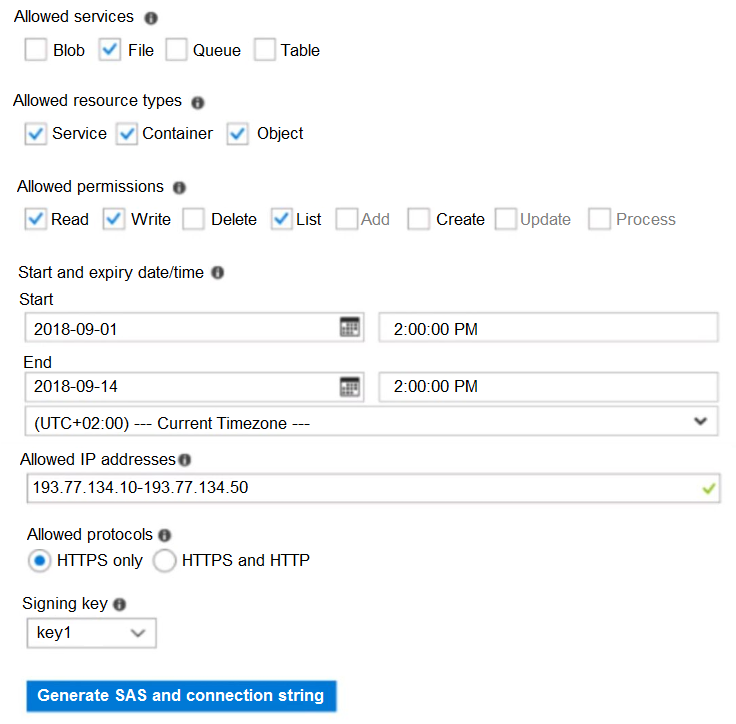
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
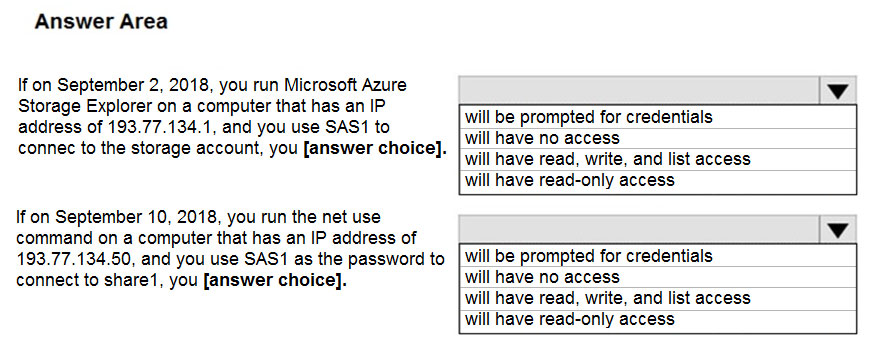
Hot Area:
Explanations
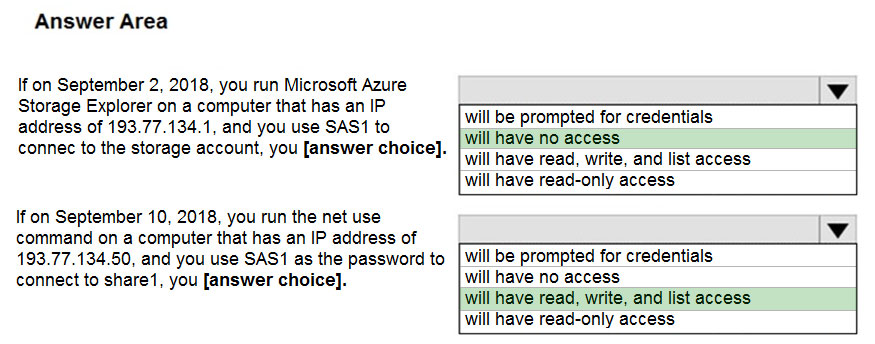
Box 1: Will have no access -
The IP 193.77.134.1 does not have access on the SAS.
Box 2: Will have read, write, and list access
The net use command is used to connect to file shares.
https://docs.microsoft.com/en-us/azure/storage/common/storage-dotnet-shared-access-signature-part-1 https://docs.microsoft.com/en-us/azure/vs-azure-tools-storage-manage-with-storage-explorer?tabs=windows