Question 15 of 267 from exam AZ-303: Microsoft Azure Architect Technologies
Question
DRAG DROP -
You have an Azure subscription that contains two virtual networks named VNet1 and VNet2. Virtual machines connect to the virtual networks.
The virtual networks have the address spaces and the subnets configured as shown in the following table.
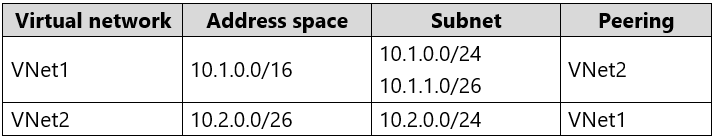
You need to add the address space of 10.33.0.0/16 to VNet1. The solution must ensure that the hosts on VNet1 and VNet2 can communicate.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Explanations
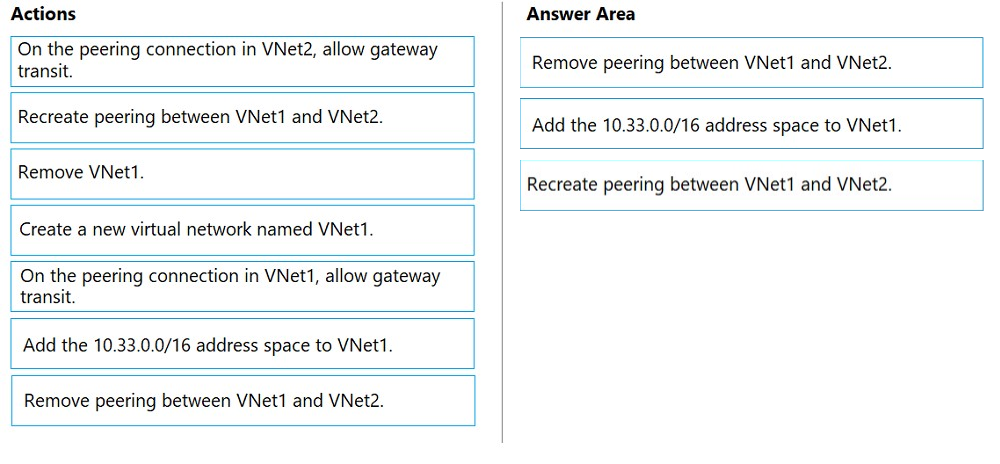
Step 1: Remove peering between Vnet1 and VNet2.
You can't add address ranges to, or delete address ranges from a virtual network's address space once a virtual network is peered with another virtual network.
To add or remove address ranges, delete the peering, add or remove the address ranges, then re-create the peering.
Step 2: Add the 10.44.0.0/16 address space to VNet1.
Step 3: Recreate peering between VNet1 and VNet2
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering