Prevent Users from Accessing Azure Portal and PowerShell
Question
You have an Azure Active Directory (Azure AD) tenant linked to an Azure subscription. The tenant contains a group named Admins.
You need to prevent users, except for the members of Admins, from using the Azure portal and Azure PowerShell to access the subscription.
What should you do?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.B
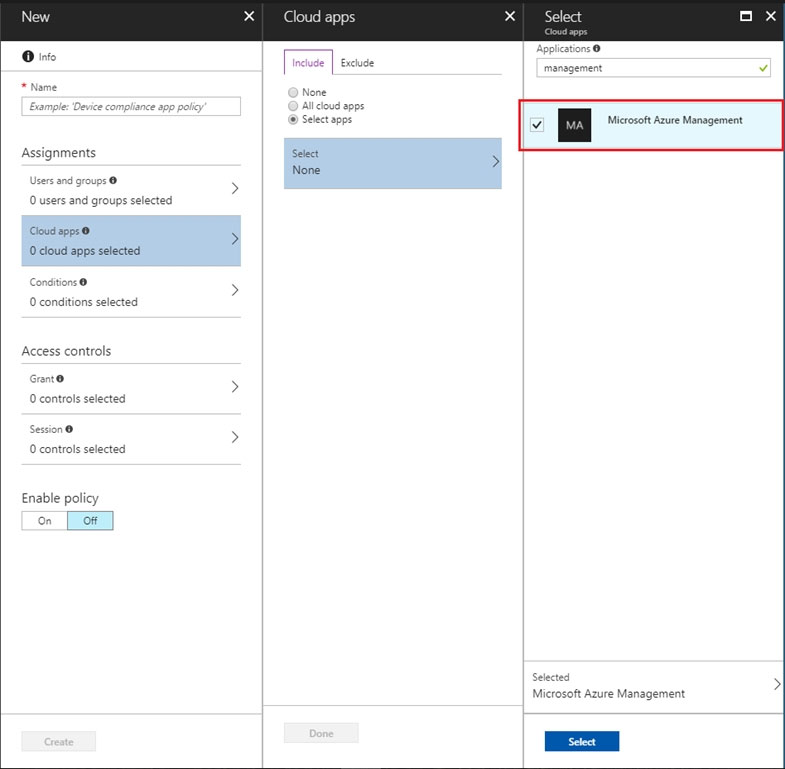
Typically, you use Conditional Access to control access to your cloud apps. You can also set up policies to control access to Azure management.
The policy you create applies to all Azure management endpoints, including the following:
-> Azure portal
-> Azure Resource Manager provider
Classic Service Management APIs -

-> Azure PowerShell
-> Visual Studio subscriptions administrator portal
-> Azure DevOps
-> Azure Data Factory portal
To create a policy for Azure management, you select Microsoft Azure Management under Cloud apps when choosing the app to which to apply the policy.
Incorrect Answers:
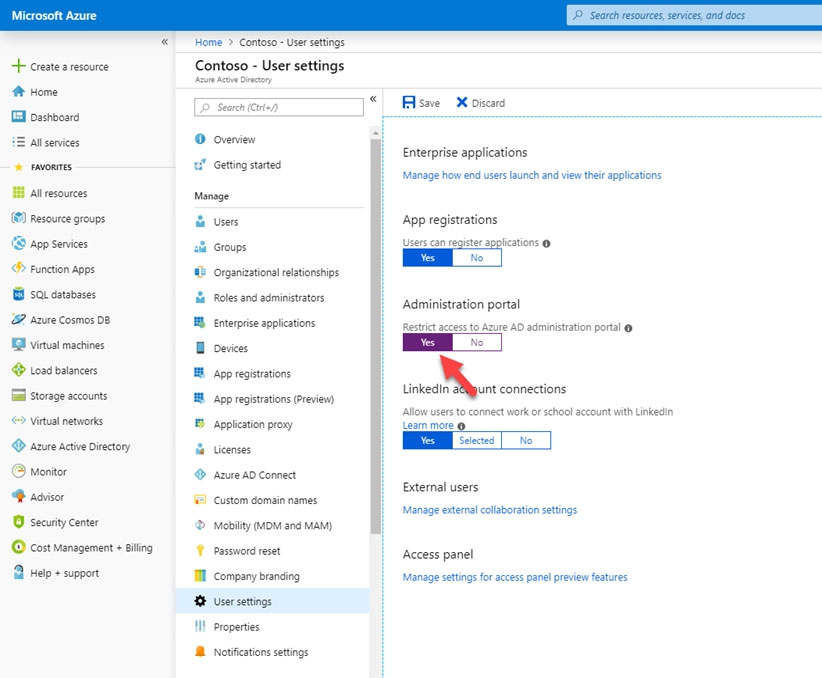
A: From User Settings you can only restrict access to Azure Portal, not access to Azure Powershell.
Note: Microsoft allows restricting standard user access to Azure Active Directory administration portal.
1. Log in to Azure portal as Global Administrator
2. Go to Azure Active Directory | User Settings
3. Then click on Yes under Restrict access to Azure AD administration portal
The correct answer to the question is D. From the Azure subscription, configure Access control (IAM).
Explanation: To prevent users, except for the members of Admins, from using the Azure portal and Azure PowerShell to access the subscription, we can configure access control (IAM) on the subscription level.
Access control (IAM) is used to manage access to resources in Azure. With access control (IAM), you can grant permissions to users, groups, and applications at a certain scope, such as the subscription level. This means you can configure access control (IAM) to grant access to only the members of the Admins group, and deny access to all other users.
To configure access control (IAM) on the subscription level, follow these steps:
- In the Azure portal, navigate to the subscription that you want to configure.
- Click on "Access control (IAM)" in the left-hand menu.
- Click on "Add" to add a new role assignment.
- In the "Add role assignment" pane, select "Owner" or "Contributor" as the role, depending on the level of access you want to grant to the members of the Admins group.
- In the "Select" box, search for the "Admins" group and select it.
- Click "Save" to save the new role assignment.
After completing these steps, only the members of the Admins group will have access to the Azure portal and Azure PowerShell to access the subscription. All other users will be denied access.
Option A: From Azure AD, configure the User settings is incorrect because it is used to configure user-specific settings, such as password policies and user consent settings.
Option B: From Azure AD, create a conditional access policy is incorrect because it is used to define conditions under which users are granted access to resources. It is not used to restrict access to resources.
Option C: From the Azure subscription, assign an Azure policy is incorrect because Azure policy is used to enforce rules and effects on resources in Azure. It is not used to manage access to resources.