Question 72 of 197 from exam AZ-100: Microsoft Azure Infrastructure and Deployment
Question
HOTSPOT -
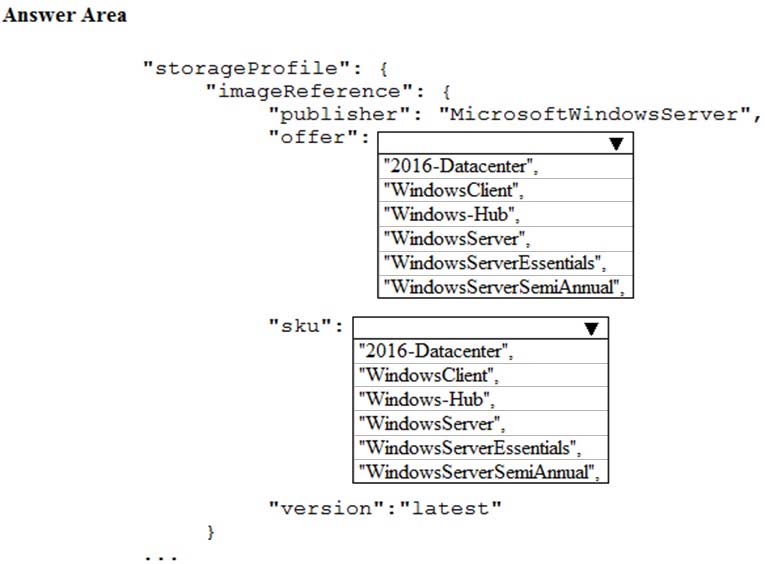
You plan to deploy 20 Azure virtual machines by using an Azure Resource Manager template. The virtual machines will run the latest version of Windows Server
2016 Datacenter by using an Azure Marketplace image.
You need to complete the storageProfile section of the template.
How should you complete the storageProfile section? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Explanations
"
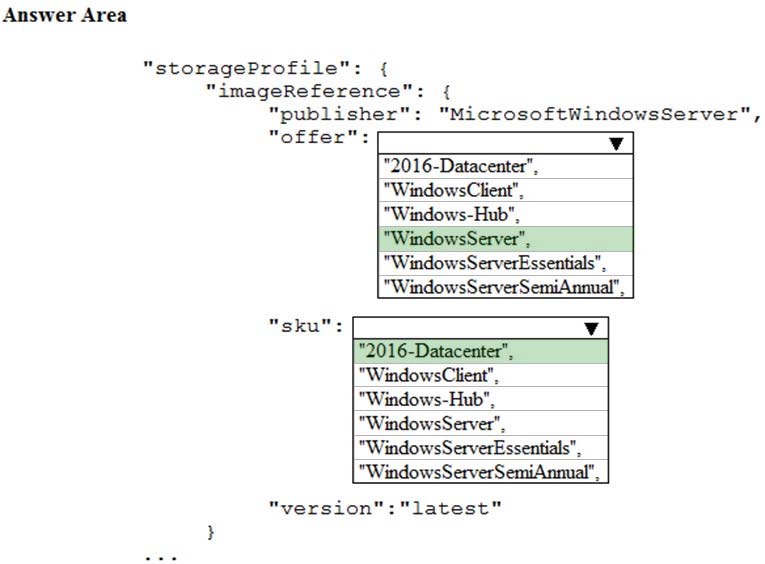
"storageProfile": {
"imageReference": {
"publisher": "MicrosoftWindowsServer",
"offer": "WindowsServer",
"sku": "2016-Datacenter",
"version": "latest"
},
"
https://docs.microsoft.com/en-us/rest/api/compute/virtualmachines/createorupdate